Enhancing OT Security with ISA/IEC 62443 Standards
Enhancing OT Security with ISA/IEC 62443 Standards
What is ISA/IEC 62443?
The ISA/IEC 62443 series of standards, developed by the International Society of Automation (ISA) and the International Electrotechnical Commission (IEC), provides a comprehensive framework for securing Industrial Automation and Control Systems (IACS). These standards are recognized globally for their holistic approach to cybersecurity, bridging the gap between operations and information technology, and integrating process safety with cybersecurity.
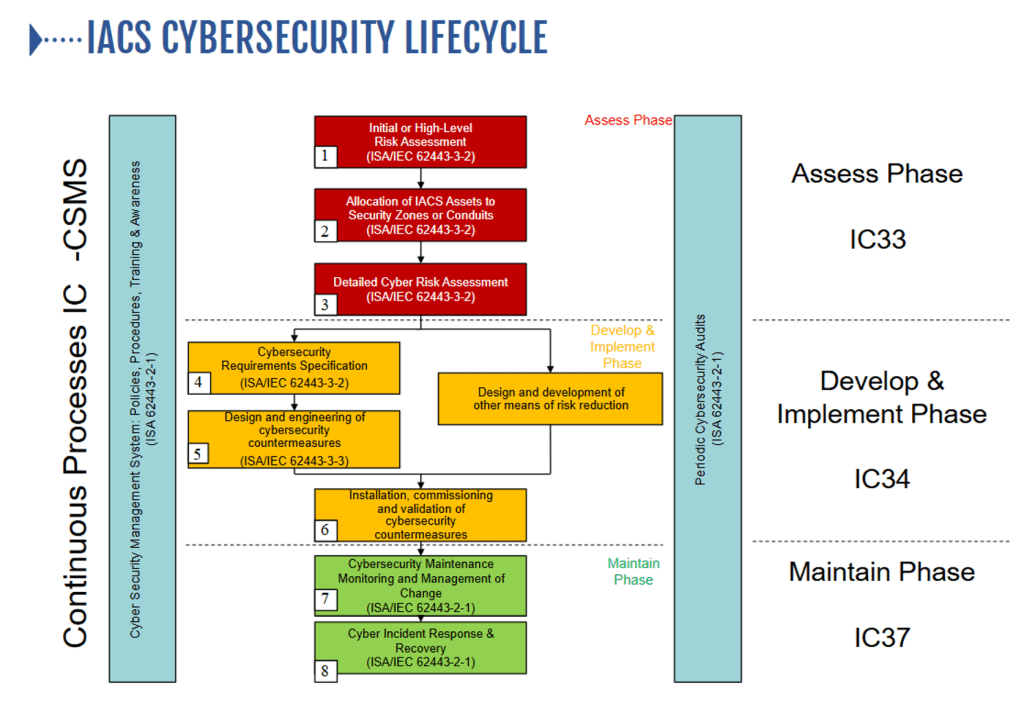
Our Approach to OT Security
At Securemation, we adopt the ISA/IEC 62443 standards to ensure that our OT security solutions are both effective and compliant. Our approach includes:
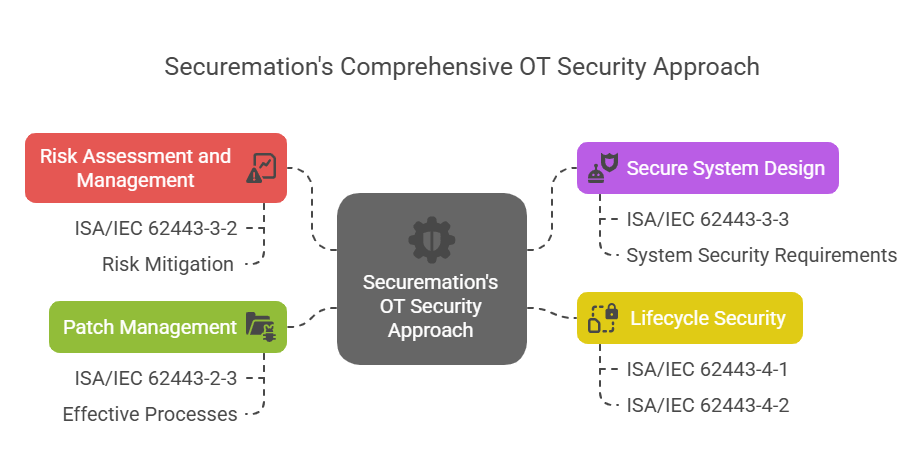
- Risk Assessment and Management: We conduct thorough risk assessments to identify potential vulnerabilities within your IACS environment. Using ISA/IEC 62443-3-2, we design security measures tailored to mitigate identified risks
- Secure System Design: Leveraging ISA/IEC 62443-3-3, we implement system security requirements and define security levels to ensure that your systems are protected against a wide range of cyber threats
- Lifecycle Security: Our security solutions encompass the entire lifecycle of your OT systems, from design and development to deployment and maintenance. We follow the guidelines of ISA/IEC 62443-4-1 and 4-2 to ensure secure product development and technical security requirements for IACS components
- Patch Management: We utilize ISA/IEC 62443-2-3 to establish effective patch management processes, ensuring that your systems remain up-to-date and resilient against emerging threats
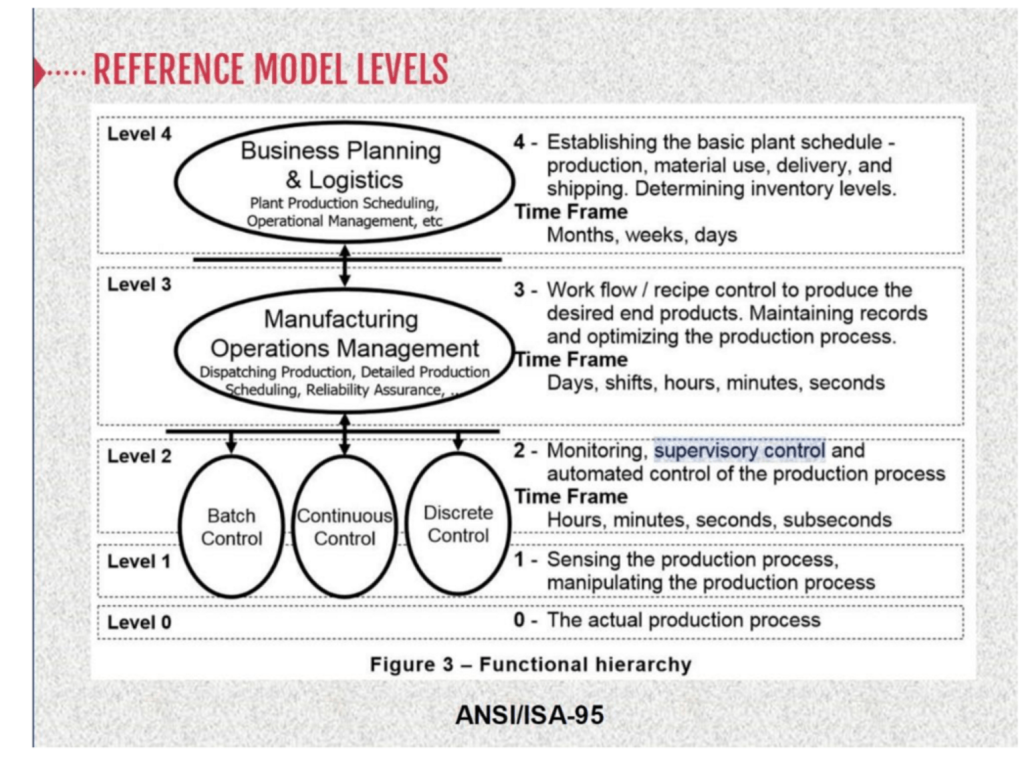
Benefits of ISA/IEC 62443 Compliance
By adhering to the ISA/IEC 62443 standards, we provide our clients with:
- Enhanced Security Posture: Our solutions help you achieve a higher level of security performance, protecting your critical infrastructure from cyberattacks.
- Regulatory Compliance: Compliance with ISA/IEC 62443 ensures that your OT systems meet industry best practices and regulatory requirements.
- Operational Continuity: Our security controls are designed to minimize disruptions, ensuring the continuous and safe operation of your industrial processes.
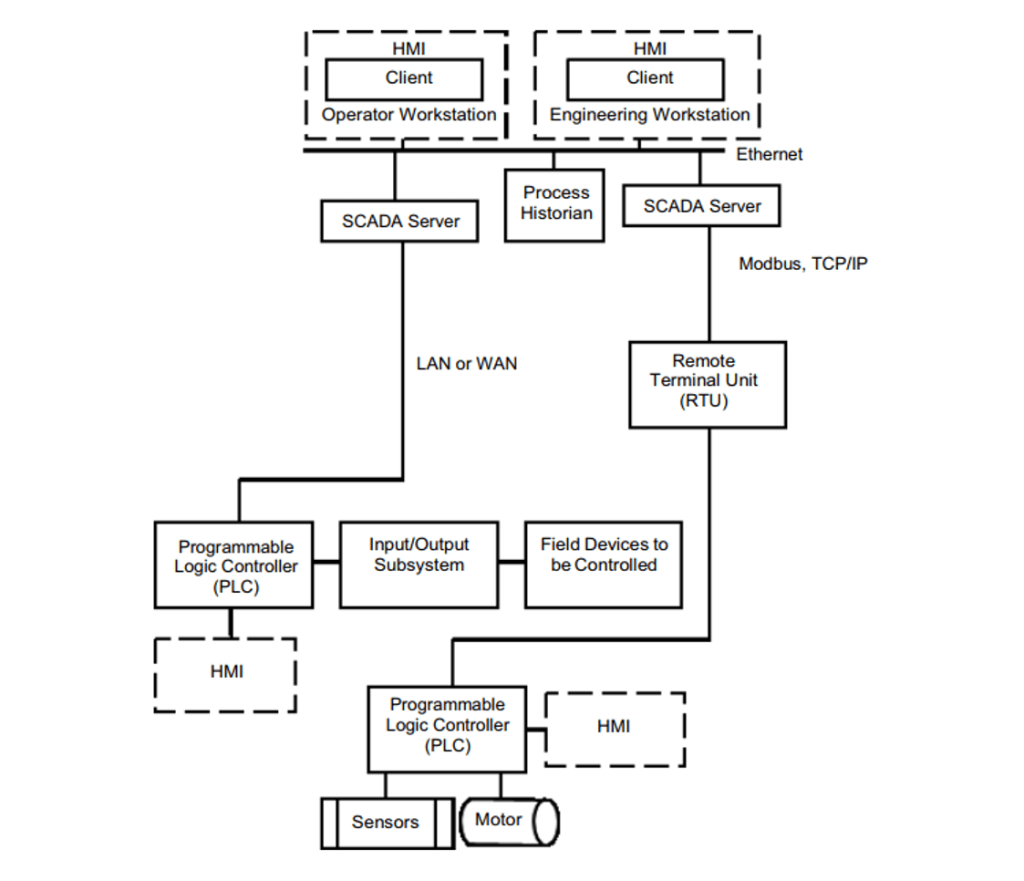
Key feature
Increased effectiveness and consistency of identifying, assessing, and treating cyber security risks across all business units.
Increased agility in decision making to suit the individual business unit's speed of service delivery.
Appropriate protection of sensitive data and increased compliance with external/internal legal and statutory requirements.
What Our Clients Say About Us
Security requirements are different in every situation. The staff, processes, location, assets, etc. may vary from one business unit to another within the same organisation. These variations create a unique environment that will therefore have unique risks, threats, and procedures to manage. However, standardised processes can be utilised to achieve the desired outcomes. The Securemation approach is to develop an optimal and customised ISMS. This involves starting with creating a solid foundation and understanding the current state of the systems, information assets, processes, risks, and controls needed by the organisation and each of its business units.
